Incident Response: Third-Party Breach
Here are the key takeaways from this blog: Vendor trust isn't security—verify everything. Embed cybersecurity requirements into contracts, conduct...

In the world of cybersecurity, incident response management is a critical component of protecting your organization's data. When an incident occurs, it is important to have a plan, specifically tailored to your organization, in place to quickly and effectively respond. This plan should include steps for identifying the incident, containing the damage, eradicating the threat, and recovering any lost data. It should also include the development of policies and procedures, the creation of specific incident response plans, and the training of team members.
Make sure you have all the following in place to take a proactive approach to managing your organization’s incident response.
IT Risk Assessment
Conducting a thorough and quality risk assessment will help to prioritize security issues, identify which are the most sensitive assets, and which critical security incidents the team should focus on.
The Incident Response Team
No one CISO or vCISO can be your whole incident response team. Since we all know it’s not a matter of if, but when, it’s important for all cybersecurity programs to assemble a well-thought-out contingency of responders. Your team should be composed of individuals with the necessary skills and knowledge to effectively respond to incidents. The team needs to have access to the resources needed to execute the incident response plan and each person should know exactly what their role and responsibilities are.
Establish Your Procedures
Next, you need to establish the procedures that will be followed in the event of an incident. You should have several plans prepared ahead of time for potential scenarios such as malware, denial of service attacks, or a phishing attack. This includes steps like identifying it and determining its scope, notifying the appropriate personnel, activating the incident response team, containing the breach, mitigating the damage, and preventing it from happening again in the future. This usually involves implementing new security controls and procedures. You should also create a communication plan to ensure that all stakeholders are kept up to date on the latest developments.
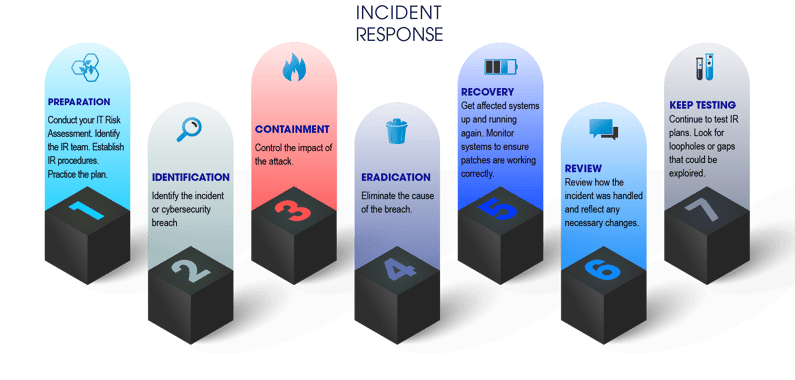
Practice, Practice, Practice
Your incident response plan on paper is just a theory and theories must be tested. Be sure to exercise your plan with the team in planned and unplanned drills. Take this opportunity to uncover weak spots and make sure everyone is confident with their role.
While incident response management is a critical part of cybersecurity, it is only one piece of the puzzle. In order to truly protect your organization's data, you need to have a comprehensive security strategy that includes prevention, detection, and response. By taking a holistic approach to security, you can make sure that your organization is prepared for anything.
Rivial Platform
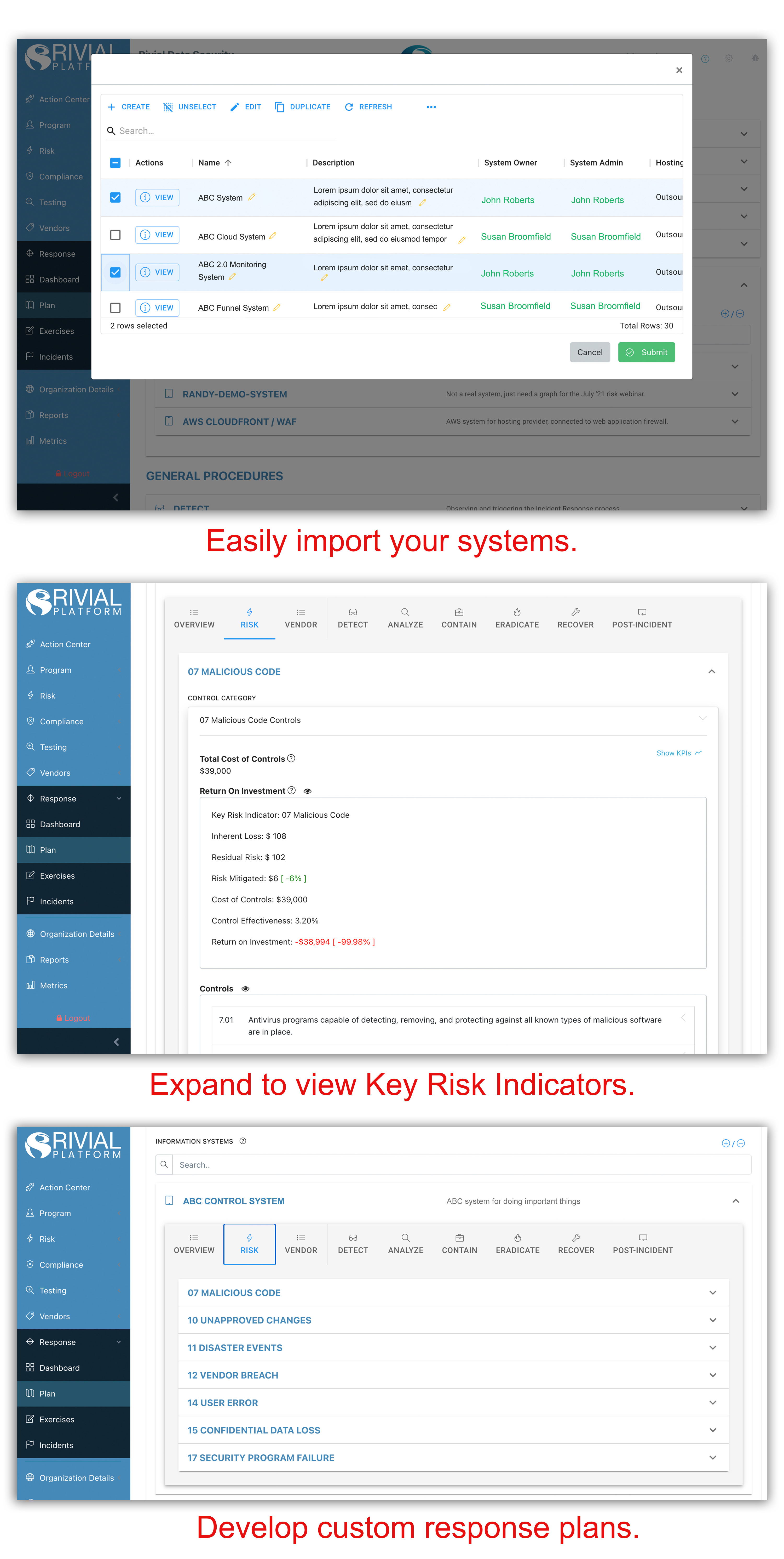
We would be remiss if we didn’t take this opportunity to share with you how easy it is to use the Rivial Platform to plan, practice, and respond to incidents across all elements of your security program. This is where you will build your incident response plan, populate the team(s), and store your policies, escalation path, detections, and systems. Build your general procedures with the detect, analyze, contain, eradicate, recover, and post-incident steps.
Risk and Response are seamlessly integrated in the Rivial Platform. From inside the Response module, it’s simple to add systems that live in the Risk module that you’d like to include in your IR plan. Without ever leaving the Response module, you can examine key risk indicators of each system to determine which systems should be added. You can then create specific steps in your playbooks that apply directly to that system. This risk-incident response integration provides a natural system of checks and balances for your risk assessment.
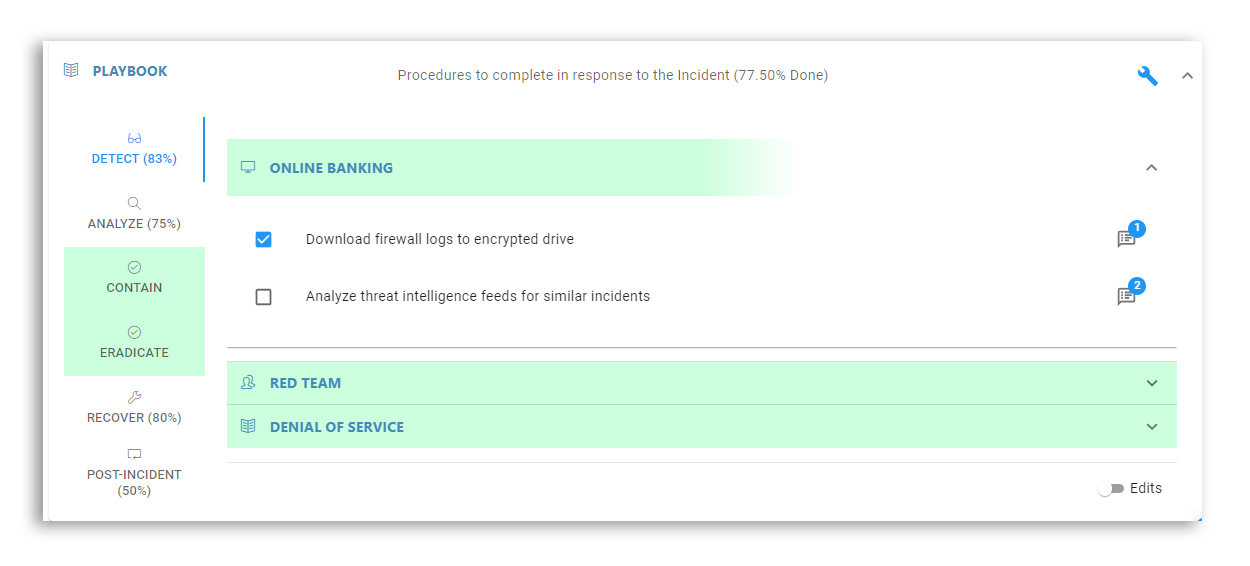
You can also set up a specific scenario, such as ransomware, to respond to in the playbooks section. Then you can exercise your plan by creating your own exercises using injections and objectives, and observations and recommendations that will tie into audit findings, teams, and documents.
In the unfortunate event of an actual realized threat, use the Rivial Platform to respond. Select the playbook sections you want to use and check off each section. When all sections are green, you have finished your incident response. You will also see any action items that came out of your incident response process and you can upload any pertinent documents.
If you’d like to learn more about how to use the Rivial Platform for a holistic and proactive approach to incident response, join us for a demo.
Here are the key takeaways from this blog: Vendor trust isn't security—verify everything. Embed cybersecurity requirements into contracts, conduct...

1 min read
Here are the key takeaways from this blog: Ransomware attacks are more sophisticated and costly than ever, with 2023 payouts exceeding $1 billion...

1 min read
Here are the key takeaways from this blog: Tailor your IR plan to your organization’s size, data sensitivity, and industry-specific...