
5 min read
How to Conduct a Vendor Security Assessment
Here are the key takeaways from this blog:
Read MoreLucas Hathaway has 10+ years of experience in information security. He is the Chief Revenue Officer at Rivial Data Security. He has worked with Rivial clients for years leading the consulting team and now leads the growth team with a focus on client success ensuring that Rivial’s platform exceeds client expectations.

5 min read
Here are the key takeaways from this blog:
Read More
6 min read
Here are the key takeaways from this blog:

5 min read
Here are the key takeaways from this blog:

3 min read
Here are the key takeaways from this blog:

4 min read
Here are key takeaways from the blog: Credential and Ransomware Attacks Dominate: Financial institutions face increasing threats from stolen...

4 min read
Here are key takeaways from the blog: Understanding Shared Responsibility is Foundational: Moving to the cloud changes the security paradigm....
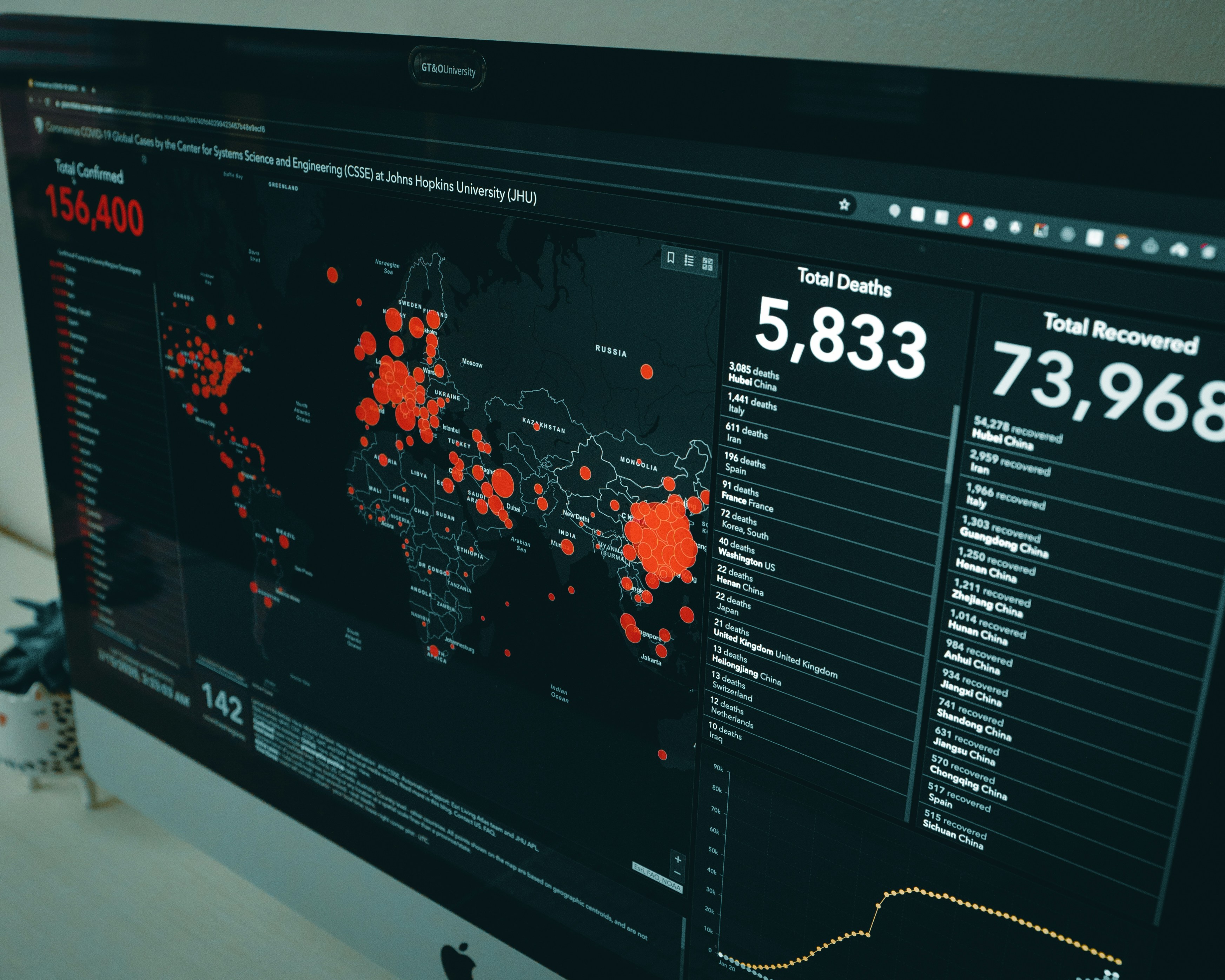
3 min read
Here are the key takeaways from this blog: Vendor trust isn't security—verify everything. Embed cybersecurity requirements into contracts, conduct...

4 min read
Here are the key takeaways from the blog: