Incident Response: Third-Party Breach
Here are the key takeaways from this blog: Vendor trust isn't security—verify everything. Embed cybersecurity requirements into contracts, conduct...

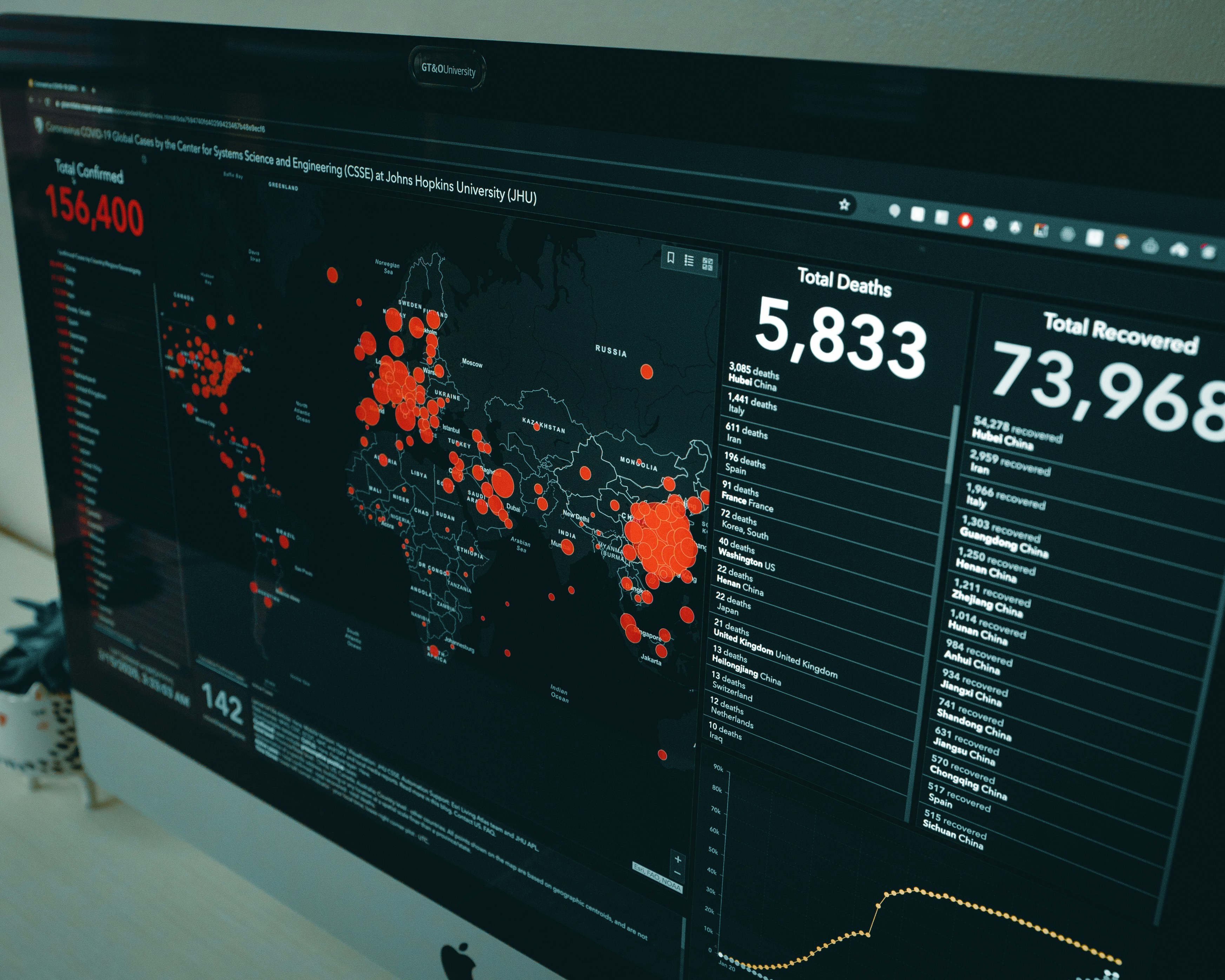
Cyber incidents are escalating in speed, impact, and cost, pushing incident response to the board level while regulators demand continuous readiness through mature, well-documented programs. By combining automation, AI-driven response, and end-to-end incident management, platforms like Rivial help organizations reduce response time, meet compliance expectations, and respond with confidence.
Key takeaways from this article:
Watch our on-demand video on how to build a regulatory-ready incident response plan below!
Zero-day ransomware, supply chain breaches, and compliance crackdowns have made incident response (IR) platforms a must-have—not a nice-to-have. In 2025, forward-leaning IR tools blend real-time detection, automated playbooks, AI triage, and audit-ready reporting into unified workflows that empower both technical teams and executives.
Below we spotlight the leading IR platforms that are setting the bar across enterprise, government, healthcare, and financial sectors—each designed to shrink dwell time, accelerate containment, and ensure regulatory alignment.
Here are the leading cybersecurity incident response platforms:

Rivial’s one-click Incident Response Plan Builder allows organizations to create personalized incident response playbooks aligned with any security framework (NIST, PCI, HIPAA, ISO, GDPR, etc.) —ideal for regulated sectors like finance, healthcare, and education.
Key Features

Cortex XSOAR stands out for its massive integration library, combining orchestration, case management, and threat intelligence into scalable IR automation.
Key Features:

Built into the Falcon platform, Fusion enables automated, conditional response workflows directly tied to endpoint activity—minimizing mean time to respond (MTTR).
Key Features

If you’re deep in the Microsoft ecosystem, Sentinel delivers a powerful, cloud-native SIEM+SOAR combo with rich analytics and native integrations.
Key Features

Ideal for mature security programs, QRadar SOAR focuses on incident orchestration, threat case management, and collaborative response.
Key Features

With its acquisition of Phantom, Splunk’s SOAR tool remains a go-to for security teams needing deep playbook customization and large-scale data ingestion.
Key Features

Trellix delivers cross-surface detection and response, helping teams correlate incidents across email, endpoint, network, and cloud.
Key Features

For organizations without a 24/7 SOC, Arctic Wolf combines human-led IR support with platform-based visibility, perfect for mid-sized companies.
Key Features:

Cyware’s platform links threat intelligence platforms (TIPs) directly with SOAR, empowering teams to act on shared intel in real time.
Key Features

Now part of Google, Siemplify offers lightweight but powerful IR orchestration, well-suited for teams already leveraging Chronicle or other Google Cloud tools.
Key Features
Certifications & Compliance Alignment
Pick a platform that aligns with the playbooks and rules you already follow—NIST 800-61, ISO/IEC 27035, NIST CSF, ISO 27001, PCI DSS 12.10, HIPAA Security, and emerging mandates like SEC cyber-disclosure, NIS2, and DORA. Native mappings and report templates (e.g., regulator-ready timelines, evidence logs) shorten audits and speed post-incident reporting.
Pricing & Contract Flexibility
Vendors price by users, automation/playbook packs, data ingestion (events per day), or incident volume. Expect enterprise suites in the $4,000–$20,000/month range depending on SOC size, SOAR add-ons, and premium threat-intel feeds. Look for flexible terms (burst licensing for major incidents), transparent overage rates, and capped renewals.
Integration Footprint
Your IR stack must snap into SIEM, EDR/XDR, firewalls, email security, cloud (AWS/Azure/GCP), IdP (SSO/MFA), ticketing/ITSM, and collaboration tools (Slack/Teams). Pre-built connectors, open APIs, and STIX/TAXII support reduce deployment time and prevent data silos; bonus points for sandbox/detonation and intel enrichment (MISP, VirusTotal).
Scalability & Performance
Choose software that won’t stall during alert storms or coordinated attacks. Look for elastic cloud architecture, horizontal scaling, high-concurrency case management, sub-second search across large evidence sets, and strong references from organizations with high EPS and global SOCs.
Automation, Orchestration & AI Capabilities
Modern IR platforms should auto-enrich, auto-contain, and auto-notify: think playbooks for credential resets, host isolation, IP/domain blocking, and IR comms. AI/ML can cluster alerts, summarize cases, and draft incident timelines—cutting MTTR while preserving analyst oversight. Ensure every automated action is logged with full rollback and approvals.
Evidence Handling, Reporting & Chain-of-Custody
Incidents live or die on documentation. Prioritize platforms with immutable timelines, artifact hashing, legal hold/eDiscovery exports, and role-based access controls. One-click regulator reports (SEC/CIRCIA/NIS2), executive summaries, and post-mortem templates keep stakeholders aligned.
User Training & Support Ecosystem
Favor vendors that offer role-based training, tabletop exercise kits, IR certifications, and 24/7 P1 support SLAs. Built-in simulators and purple-team scenarios help you test playbooks before you need them, keeping analysts sharp and executives confident.
By weighing these factors up front, you’ll select incident response software that matches today’s attack velocity, meets tomorrow’s regulatory deadlines, and measurably drives down MTTR.
Ready to turn alert chaos into calm, coordinated response? Rivial Data Security pairs an all-in-one Incident Response Management platform with seasoned responders who operate as an extension of your team.
Don’t wait for the next breach to set the narrative. Schedule a demo of Rivial’s Incident Response platform today and see how fast, audit-ready response can be.
Watch our on-demand video on how to build a regulatory-ready incident response plan below!
Here are the key takeaways from this blog: Vendor trust isn't security—verify everything. Embed cybersecurity requirements into contracts, conduct...

1 min read
Here are the key takeaways from this blog: Know the Regulatory Definitions and Deadlines — NCUA and FDIC have strict criteria and timelines (72 and...

1 min read
Cyber threats are accelerating, making proactive, well-tested incident response programs essential as regulators demand documented and practiced...