1 min read
Frameworks to replace FFIEC’s CAT
Here are the key takeaways: FFIEC CAT retirement by August 2025: With the Cybersecurity Assessment Tool being phased out, institutions should begin...

In October of this year the Federal Financial Institutions Examination Council (FFIEC) released a Frequently Asked Questions (FAQ) Guide for the Cybersecurity Assessment Tool (CAT). Aside from forcing me to cram a large amount of acronyms into the title of this article, what does the FAQ tell us?
The most important question and response to me was whether or not institutions must use the tool. Since Day 1 the FFIEC has maintained the stance that the tool is voluntary. The direct response in the FAQ is “No. Use of the Assessment by institutions is voluntary. Institution management may choose to use the Assessment, or another framework, or another risk assessment process to identify inherent risk and cybersecurity preparedness.”
Many of our financial institution clients have been asked to provide the results of their CAT assessment. And in many cases the examiner’s approach certainly does not make the tool feel voluntary in any way. The way the CAT results are being treated by examiners makes the tool seem like a hard and fast requirement.
In theory, an institution could use the response above from the FAQ to argue their point. But arguing with an examiner right out of the gate is usually not a great approach. And as I mentioned previously, the FFIEC has called the tool mandatory since its release in June 2015. At Rivial we incorporated the CAT control framework into our risk assessments and IT audits to help our clients.
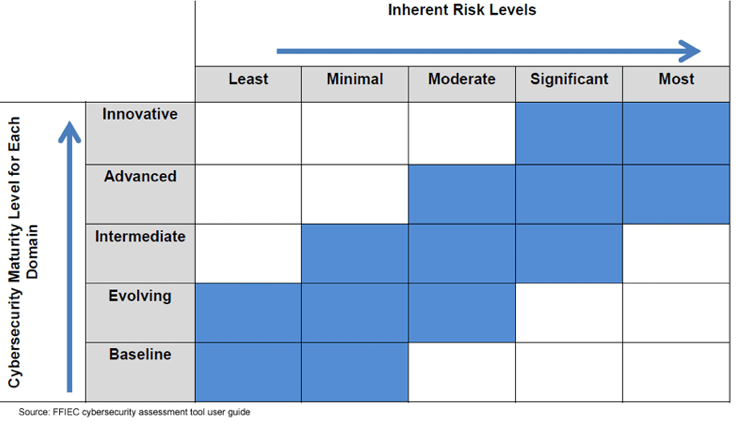
In addition to some basic Q&A throughout the FAQ Guide, there is a very useful section that clears up a few concepts from the Inherent Risk Profile. To help clients answer these questions, I did some research last year and drew some conclusions about what they were really asking. Thank you to the FFIEC for providing some additional information so others don’t have to do the same research I did:
Trust services: Thought of broadly to include fiduciary services for individual clients (e.g. personal trusts and investment management accounts) and corporate clients (e.g., employee benefit plans, endowments/foundations, and bond issuances), non-fiduciary services (e.g. retail brokerage, custody services [securities, cash and documents], and security-holder services [transfer agent]). Also may be referred to as asset management products and services.
Merchant acquirer: Merchant acquirers sponsor merchants in the retail payments system as members of the credit card association. (Source: FFIEC Retail Payment Systems Booklet) Global remittance providers: A global remittance or a remittance transfer includes most electronic money transfers sent by consumers in the United States through remittance transfer providers to recipients in other countries. (Source: Regulation E, 12 CFR 205)
Treasury services: A broad collection of services, including but not limited to cash management, liquidity management, trade finance, and information services, offered to corporate or business clients. These services are typically offered through an investment bank.
If you want more information about FFIEC requirements or the CAT, drop us a line at info@rivialsecurity.com. Or you can Join the Club using the form to the right.
Happy CATing!

1 min read
Here are the key takeaways: FFIEC CAT retirement by August 2025: With the Cybersecurity Assessment Tool being phased out, institutions should begin...

1 min read
Here are the key takeaways from this blog: FFIEC will retire the Cybersecurity Assessment Tool (CAT) by August 2025, urging financial institutions...